The Intersection of Cybersecurity and Web Development: Best Practices for Secure Web Applications
In recent years there has been rapid growth in web applications development. There have been widespread adoptions of web applications integrated into almost all aspects of our work and entertainment, as the digital landscape has become an integral part of our daily lives. The landscape of web development tools and frameworks is vast (To mention a few of them that are popular: React, Angular, Vue, Next, Laravel, Flask, Django, and Ruby) and they are still continuously evolving.
While the continuous and rapid evolution enables developers to build innovative and feature-rich applications, it also introduces new attack surfaces for cybercriminals. Therefore, developers must stay up-to-date with the latest security trends, emerging threats, and industry best practices to fortify their web applications effectively.
As cyber threats evolve in sophistication and frequency, the importance of integrating security into the web development process cannot be overstated. Traditionally, security was often considered an afterthought, with many developers focusing primarily on functionality and user experience. However, this approach left web applications vulnerable to cyberattacks, leading to data breaches/leaks, identity theft, and other malicious activities, and as the architects behind these web applications, web developers play a pivotal role in ensuring security in their applications and protecting users' data and privacy. The intersection of cybersecurity and web development represents the crucial juncture where developers can implement best practices to build robust and secure web applications.
In response to the growing threatscape, the concept of "security by design" has gained prominence in the world of web development. This paradigm shift emphasizes integrating security principles from the very inception of a web application's development. By incorporating security considerations early on, developers can preemptively address potential vulnerabilities and ensure a stronger foundation for their applications.
Beyond secure coding, user authentication and access control mechanisms are pivotal in safeguarding web applications from unauthorized access. Ensuring that only authenticated users can access sensitive data or perform critical actions adds an extra layer of protection, and with web applications increasingly relying on APIs and web services - Proper API authentication, rate limiting, and input validation are vital for mitigating potential API-related threats.
Despite the best efforts to create secure applications, vulnerabilities may still emerge. To handle such situations effectively, the collaboration between web developers and cybersecurity experts is crucial to enhance the security posture of web applications. Penetration testers and ethical hackers can help identify potential vulnerabilities through controlled testing, enabling developers to remediate these issues proactively. Security professionals can also provide valuable insights into emerging threats and assist in the implementation of appropriate security controls.
Beyond the technical aspects, web developers must prioritize user education about cybersecurity. By integrating user-friendly security features and providing guidance on best security practices, developers can empower users to take an active role in safeguarding their online activities. This includes promoting strong password practices, enabling multi-factor authentication, and raising awareness about phishing and social engineering attacks.
Now let's look deeper into how we can mitigate risks when developing web applications.
1️⃣ Security by Design & Secure Coding Practices
Security by design is an approach to software and hardware development that seeks to make systems as free of vulnerabilities and impervious to attack as possible through such measures as continuous testing, authentication safeguards, and adherence to best programming practices.
For example, while developing an online banking application or an online shopping website - where there will be many transactions, and where the application holds susceptible data such as PII (Personal Identifiable Information) and banking information/credit card information, there needs to be a tight hold on security measures from the very beginning. Even the smallest weak link will prove to be an advantage for an attacker and a nightmare to the user.
Critical Application Security Risks:
Numerous security design principles have been proposed to direct security decisions. We will discuss two of them in this section. The first one is OWASP and the second one is NIST.
OWASP (Open Web Application Security Project)
The Open Web Application Security Project (OWASP) is a nonprofit foundation that guides how to develop, purchase and maintain trustworthy and secure software applications. OWASP is noted for its popular Top 10 list of web application security vulnerabilities.
The developer community's consensus on the top security dangers forms the basis of the OWASP Top 10 list of security vulnerabilities. Every few years, it is revised when new and changing dangers are identified. The list describes the most harmful web application security holes and offers suggestions for how to fix them.
The first version of the OWASP Top 10 list was published in 2003. Updates followed in 2004, 2007, 2010, 2013, and 2017. The most recent update was published in 2021.
The goal of OWASP is to inform business owners, developers, designers, and architects about the dangers posed by the most prevalent online application security flaws. Both open-source and for-profit security products are supported by OWASP. It is renowned as a venue where security specialists and IT professionals can connect and exchange knowledge.
OWASP TOP 10: Then & Now | |
2003 | 2021 |
Unvalidated Parameter | Broken Access Control |
Broken Access Control | Cryptographic Failures |
Broken Account & Session Management | Injection |
Cross-site Scripting Flaws | Insecure Design |
Buffer Overflows | Security Misconfiguration |
Command Injection Flaws | Vulnerable & Outdated Components |
Error Handling Problems | Identification & Authentication Failures |
Insecure use of Cryptography | Software & Data Integrity Failures |
N/A | Security Logging & Monitoring Failures |
Web Application Server Misconfiguration | Server-side Request Forgery |
OWASP Top 10 security risks, 2021:
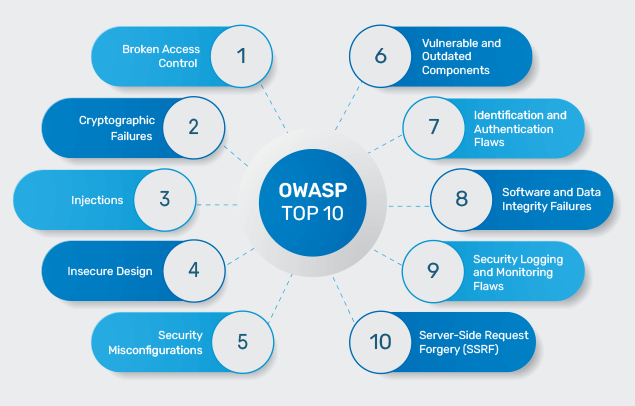
- Broken access control: Attackers can bypass access controls by elevating their permissions or in some other way, giving unauthorized access to data or systems. This has become the top security risk and was created by combining two categories.
- Cryptographic failures: Vulnerabilities occur when cryptographic methods aren't used appropriately for data protection.
- Injection: Attackers can insert data in an application that includes malicious commands, redirect data to a malicious website, or change the application itself.
- Insecure design: System architecture design flaws cause issues when an application is developed using an insecure authentication process or isn't built to prevent bot attacks.
- Security misconfiguration: Problems with security configuration facilitate attacks, such as by enabling the use of default user IDs, passwords, or authorizations.
- Vulnerable & outdated components: Developers may use software components with vulnerabilities in applications or unpatched, out-of-date software.
- Identification & authentication failures: These vulnerabilities include authentication issues that enable credential stuffing and brute-force attacks.
- Software & data integrity failures: Application code and infrastructure that doesn't fully protect software or data integrity are vulnerable.
- Security logging & monitoring failures: A system not adequately monitored to detect and respond to attacks and logs kept of these events is a vulnerability.
- Server-side request forgery: Applications must perform adequate validation of user-provided resources to prevent these attacks.
To maintain a strong foundation for secure design, it's important to follow these key security principles:
✔️ Limit accessibility to only what is necessary for the given context.
✔️ Separate responsibilities and delegate control appropriately.
✔️ Establish a clear trust-building process with validation after each connection.
✔️ Use a simple system design to facilitate easy analysis.
✔️ Monitor sensitive events.
✔️ Ensure failures are secured and secure defaults are used.
✔️ Avoid relying on ambiguity.
✔️ Implement a deep defense mechanism.
✔️ Avoid creating new security technologies.
✔️ Continuously search for and address the weakest links in security.
How do we address security concerns?
Injection
Injection attacks occur when untrusted data is provided to a code interpreter via form submission or other input sources in a web application. This input is treated by the interpreter as part of a command or query, which can alter the execution of a program or application.
To prevent injection attacks, it is important to limit the length and type of text that can be entered into input fields. Additionally, ensuring that certain characters are escaped or rejected by entry fields can also be effective.
Cross-Site Scripting (XSS)
Cross-Site Scripting is another type of injection attack that allows attackers to inject client-side scripts into web pages viewed by other users. XSS can be used to bypass access controls, such as the Same-Origin Policy.
To prevent XSS attacks, precautions should be taken when rendering user input in the browser.
Broken Authentication and Access Control
The primary goal of an authentication system is to verify the authenticity of entities attempting to access a resource. Weak authentication systems can lead to breaches, enabling attackers to gain access to user accounts or compromise an entire system through an administrator account.
Mitigate authentication vulnerabilities by implementing two-factor authentication (2FA) and implementing limitations or delays on repetitive login attempts. Allowing password entry from password safes via paste and drag and drop can also support strong and unique passwords.
Sensitive Data Exposure
Sensitive data such as passwords and financial information (credit card numbers, personally identifiable information) must be protected to prevent attackers from using them for malicious purposes. For example, in a Man-in-the-Middle (MITM) attack, an attacker eavesdrops or impersonates to intercept valuable information under the guise of normal data exchange.
Protect user data by encrypting sensitive information and avoiding unnecessary data storage.
Broken Access Control
Broken access control occurs when unauthorized users bypass authorization and perform actions reserved for privileged users. For example, an employee from a non-finance department gains access to financial or transaction records.
To address broken access control, involve UX staff in mapping out user flows related to access permissions and removing outdated pages. Also, be mindful of the URL structure to prevent manipulation and unauthorized access.
Security Misconfiguration
Security misconfigurations are common vulnerabilities that can make a system susceptible to attacks. This often occurs due to incorrect configurations or excessive display of detailed error messages, which can reveal system vulnerabilities and aid attackers.
Mitigate security misconfigurations by removing unused features from the code and displaying generalized error messages. Regularly review and update account permissions and backup authentication credentials to ensure system security.
NIST (National Institute of Standards and Technology)
The National Institute of Standards and Technology (NIST) was established in 1901 and currently operates under the U.S. Department of Commerce. It is one of the country's oldest physical science laboratories. Its creation was prompted by the need to address a significant impediment to U.S. industrial competitiveness at the time—an inadequate measurement infrastructure that lagged behind countries like the United Kingdom and Germany, as well as other economic rivals.
Numerous products and services, ranging from smart electric power grids and electronic health records to atomic clocks, advanced nanomaterials, and computer chips, rely on the technology, measurement, and standards provided by the National Institute of Standards and Technology.
Today, NIST's measurements support a wide spectrum of creations, spanning from the smallest of technologies, such as nanoscale devices that can fit tens of thousands on the end of a single human hair, to earthquake-resistant skyscrapers and global communication networks.
You can put the NIST Cybersecurity Framework to work in your business in these five areas: Identify, Protect, Detect, Respond, and Recover.
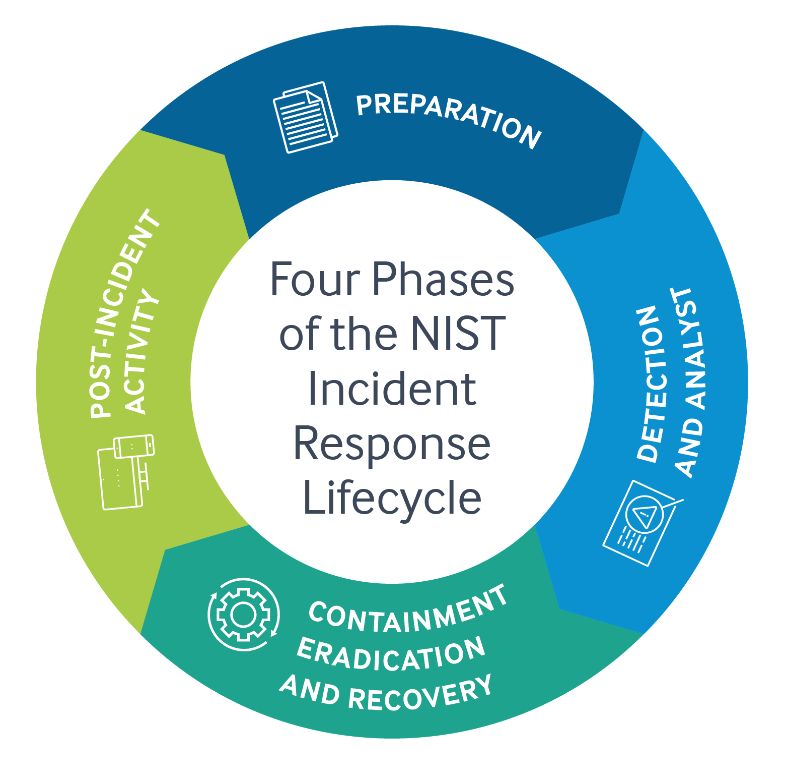
a) Identify
List all equipment, software, and data you use, including laptops, smartphones, tablets, and point-of-sale devices.
b) Protect
✔️ Control who logs on to your network and uses your computers and other devices.
✔️ Use security software to protect data.
✔️ Encrypt sensitive data, at rest and in transit.
✔️ Conduct regular backups of data.
✔️ Update security software regularly, automating those updates if possible.
✔️ Have formal policies for safely disposing of electronic files and old devices.
✔️ Train everyone who uses your computers, devices, and network about cybersecurity. You can help employees understand their risk in addition to their crucial role in the workplace.
c) Detect
Monitor your computers for unauthorized personnel access, devices (like USB drives), and software.
d) Respond
Have a plan for:
✔️ Notifying customers, employees, and others whose data may be at risk.
✔️ Keeping business operations up and running.
✔️ Reporting the attack to law enforcement and other authorities.
✔️ Investigating and containing an attack.
✔️ Updating your cybersecurity policy and plan with lessons learned.
✔️ Preparing for inadvertent events (like weather emergencies) that may put data at risk.
e) Recover
After an attack:
✔️ Repair and restore the affected equipment and parts of your network.
✔️ Keep employees and customers informed of your response and recovery activities.
2️⃣ User Authentication & Access Control
User Authentication and Access Control are two crucial elements of web application security that play a fundamental role in safeguarding sensitive data and ensuring that only authorized users can access specific resources or perform certain actions. Together, these mechanisms provide a robust defense against unauthorized access and potential security breaches.
A) User Authentication: User authentication involves verifying the identity of a user to ensure that they are who they claim to be. In web applications, this typically involves users providing credentials like a username and password, which are then validated against securely stored user data in a database. Authentication serves as the initial line of defense for web applications, preventing unauthorized individuals from gaining access to sensitive information or conducting actions on behalf of legitimate users.
Best practices for user authentication include:
- Implementing Secure Password Policies: Enforcing strong password policies that require users to create complex passwords with a combination of letters, numbers, and special characters helps protect against brute-force attacks.
- Using Multi-Factor Authentication (MFA): Adding an extra layer of security by requiring users to provide a second form of identification, such as a one-time code sent to their mobile device, in addition to their password.
- Employing Password Hashing: Storing passwords in hashed and salted form rather than plaintext ensures that even if the database is compromised, attackers cannot retrieve users' actual passwords.
- Implementing Account Lockouts & Brute-Force Protection: Enabling account lockouts after a certain number of failed login attempts prevents brute-force attacks.
- Ensuring Proper Session Management: Managing user sessions effectively ensure that users remain authenticated throughout their session and are automatically logged out after a period of inactivity.
B) Access Control: Access control determines which resources and actions users are permitted to access within a web application. It involves assigning roles and permissions to different user groups or individuals and ensuring they only have access to relevant parts of the application based on their role. Access control is vital for preventing unauthorized users from accessing sensitive data or performing prohibited actions.
Best practices for access control include:
- Implementing Role-Based Access Control (RBAC): Using RBAC allows administrators to define different roles (e.g., admin, user, guest) and assign specific permissions to each role. This simplifies access management and reduces the risk of granting unnecessary permissions to users.
- Applying the Least Privilege Principle: Granting users only the minimum privileges necessary to perform their tasks minimizes the potential damage caused by a compromised account.
- Regularly Reviewing & Updating Access Control Policies: Keeping access control policies up-to-date and reviewing them periodically ensures they align with the changing user roles and application requirements.
- Designing Secure URLs & Endpoints: Ensuring that sensitive functionalities and resources are accessible only through secure URLs or endpoints helps prevent unauthorized access.
By implementing strong user authentication and access control mechanisms, web developers can significantly bolster the security of their applications and protect users' data and privacy. Continuous monitoring and updating of these mechanisms are essential to stay ahead of evolving cybersecurity threats and maintaining a secure web environment for both users and organizations.
3️⃣ Ensuring Data Privacy & Protection

Protecting and securing user data is a crucial responsibility for web developers and organizations. To build trustworthy and compliant web applications, it is essential to implement robust data privacy and protection measures. By following these best practices, developers can instill confidence in their users, adhere to legal requirements, and mitigate the risks associated with data breaches:
- Data Encryption: Encrypt sensitive data during transmission and storage using strong encryption algorithms like AES. This ensures that even if the data is accessed without authorization, it remains unreadable to attackers.
- Secure Data Storage: Choose secure and reputable database systems with strong access controls, firewalls, and regular security updates. Additionally, encrypt sensitive data stored in the database to protect it at rest.
- Minimize Data Collection & Retention: Collect only the necessary data required for the application's functionality and avoid retaining data longer than necessary. Implement data retention policies to delete or anonymize user data when it is no longer needed.
- Compliance with Data Protection Regulations: Stay informed about data protection regulations such as GDPR and CCPA and ensure compliance with their requirements for data collection, processing, and protection.
- Secure Data Transmission: Implement secure communication protocols like HTTPS to encrypt data transmitted between the user's browser and the web server. This prevents eavesdropping and man-in-the-middle attacks.
- Access Control and Authentication: Implement robust user authentication mechanisms and access controls to limit data access based on user roles and permissions. Follow the principle of least privilege to ensure that users only have access to what they require.
- Regular Security Audits & Testing: Conduct regular security audits and vulnerability assessments to identify and address any weaknesses in the application's data privacy and protection measures. Perform penetration testing to simulate real-world attacks and evaluate the system's resilience.
- Employee Training & Awareness: Train employees on data privacy best practices, security protocols, and the responsible handling of sensitive data. Creating a culture of security awareness is essential to prevent human errors that can lead to data breaches.
- Incident Response & Data Breach Preparedness: Develop an incident response plan that outlines steps to handle and respond to potential data breaches. This includes identifying and containing the breach, notifying affected users, and taking corrective actions to prevent similar incidents in the future.
Prioritizing data privacy and protection not only protects users' sensitive information but also strengthens the reputation of web applications. By adhering to these best practices, web developers contribute to a safer digital environment where privacy is valued and respected.
4️⃣ Securing Web APIs & Services
Securing web APIs and services is extremely important in modern web development. These APIs and services play a critical role in exchanging data between different applications and systems. Without strong security measures in place, they become vulnerable to cyber threats, such as data breaches and unauthorized access. To ensure the integrity and confidentiality of data transmitted through APIs, developers must follow a comprehensive set of security practices.
- Authentication & Authorization: Implement robust authentication methods to verify the identity of users and applications accessing the API. Common methods include API keys, OAuth, and JSON Web Tokens (JWT). Additionally, use proper authorization mechanisms to grant access only to authorized users and prevent unauthorized access to sensitive functionalities and data.
- Rate Limiting & Throttling: Control the number of requests allowed from a single client over a specific period by implementing rate limiting and throttling. This helps prevent API abuse, brute-force attacks, and Distributed Denial of Service (DDoS) attacks.
- Input Validation & Sanitization: Thoroughly validate and sanitize input data to prevent injection attacks, such as SQL injection and Cross-Site Scripting (XSS). Input validation ensures that only expected and safe data is processed by the API.
- Secure Transmission: Ensure secure transmission of data between the API server and client applications by utilizing HTTPS with strong encryption algorithms (TLS/SSL). This prevents eavesdropping, man-in-the-middle attacks, and data tampering.
- API Versioning: Implement versioning for APIs to maintain backward compatibility and enable controlled updates. This helps avoid disruptions to client applications that rely on the API.
- Error Handling & Reporting: Follow proper error handling practices to avoid exposing sensitive information through error messages. Provide detailed but generic error messages to users to prevent information leakage.
- Logging & Monitoring: Implement logging and monitoring mechanisms to track API activities and detect suspicious behavior. Centralized logging can assist in identifying potential security incidents or anomalies.
- Secure Header Policies: Mitigate cross-site scripting and cross-origin request vulnerabilities by utilizing security headers like Content Security Policy (CSP), Strict Transport Security (HSTS), and Cross-Origin Resource Sharing (CORS).
- Data Validation & Integrity: Ensure the integrity of incoming and outgoing data by verifying it using hashing or digital signatures. This ensures that data remains unaltered during transmission.
- API Security Testing: Regularly conduct security testing, including penetration testing and vulnerability assessments, to identify and address potential security weaknesses.
- Access Tokens & Token Management: For OAuth-based APIs, securely manage access tokens and implement token expiration and revocation to restrict access to authorized users.
By following these best practices, web developers can significantly enhance the security of their web APIs and services. A well-secured API not only protects data but also builds trust with users and client applications, making it a crucial component in the ecosystem of interconnected web applications.
5️⃣ Handling Security Vulnerabilities
Handling security vulnerabilities is a crucial aspect of maintaining a secure and resilient web application. Despite rigorous security measures, vulnerabilities may still arise due to various factors, including software bugs, misconfigurations, or newly discovered attack vectors. Promptly identifying, assessing, and mitigating security vulnerabilities is essential to protect sensitive data, maintain user trust, and prevent potential cyberattacks. Here's a guide on effectively handling security vulnerabilities:
- Vulnerability Assessment: Perform regular vulnerability assessments using specialized tools or services to identify potential weaknesses in your web application's infrastructure, codebase, and configurations. These assessments help discover known vulnerabilities and common security issues, allowing you to address them proactively.
- Responsible Disclosure Policy: Adopt a responsible disclosure policy that encourages security researchers and ethical hackers to report vulnerabilities they discover in your application. Provide clear guidelines on how to submit vulnerability reports securely and promptly
- Swift Patching & Updates: Upon discovering a security vulnerability, act swiftly to develop and deploy patches or updates to fix the issue. Prioritize critical vulnerabilities that pose an immediate threat to your application's security.
- Communication & Transparency: Communicate openly with affected users and stakeholders about the vulnerability, its potential impact, and the steps taken to address it. Transparency fosters trust and demonstrates a commitment to maintaining a secure environment.
- Version Control & Rollbacks: Utilize version control systems to track changes and maintain a history of your codebase. This allows you to identify when and where vulnerabilities were introduced. If necessary, implement rollbacks to revert to a previous stable version until the issue is resolved.
- Continuous Security Testing: Implement continuous security testing as part of your development process. This includes static code analysis, dynamic application security testing (DAST), and regular penetration testing. Regular testing helps you identify and mitigate vulnerabilities throughout the development lifecycle.
- Third-Party Dependency Management: Regularly review and update third-party libraries and dependencies used in your application. Often, vulnerabilities in these dependencies can lead to security issues in your application. Stay informed about security patches and updates from the respective vendors.
- Security Training & Awareness: Educate your development team about secure coding practices, common security vulnerabilities, and secure design principles. Raising awareness among team members empowers them to write more secure code and detect potential security issues during development.
- Incident Response Plan: Have a well-defined incident response plan in place to handle security incidents effectively. This plan should include steps for identifying, containing, and remediating security vulnerabilities and incidents.
- Monitor Security Threats & Trends: Stay informed about the latest security threats and trends in web application security. Participate in security communities and subscribe to security advisories and alerts to be aware of emerging vulnerabilities that could affect your application.
Handling security vulnerabilities requires a proactive and vigilant approach. By establishing a robust vulnerability management process and a security-focused culture, you can significantly reduce the risk of security breaches and continuously improve the security posture of your web application.
6️⃣ Regular Security Audits & Penetration Testing
Regular security audits and penetration testing are essential components of a comprehensive cybersecurity strategy for web applications. These proactive measures are designed to assess the security posture of an application, identify potential vulnerabilities, and help developers and organizations strengthen their defense against cyber threats. Let's explore the significance and benefits of regular security audits and penetration testing:
A) Regular Security Audits:
A security audit involves a systematic examination of an application's security controls, policies, and practices. It assesses whether the application adheres to industry standards, best practices, and regulatory requirements. Regular security audits help:
- Identify Security Weaknesses: Audits reveal vulnerabilities, misconfigurations, and potential weaknesses in the application's design and implementation. This helps developers prioritize remediation efforts.
- Ensure Compliance: Audits ensure that the application complies with relevant data protection laws, industry standards, and internal security policies.
- Verify Security Controls: Audits verify the effectiveness of security controls, such as authentication mechanisms, access controls, and encryption.
- Enhance Security Awareness: Audits raise security awareness among developers and stakeholders, emphasizing the importance of security in the development process
B) Penetration Testing:
Penetration testing, often referred to as ethical hacking, involves simulating real-world cyberattacks on an application to identify exploitable vulnerabilities. The process typically includes
- Vulnerability Identification: Penetration testers identify potential vulnerabilities and weaknesses in the application's infrastructure, codebase, and configurations.
- Exploitation: Testers attempt to exploit identified vulnerabilities to understand their impact and potential consequences.
- Reporting: After the testing phase, testers provide a detailed report with findings, including the vulnerabilities discovered, the methods used to exploit them, and recommendations for mitigation.
Benefits of Regular Security Audits & Penetration Testing:
- Risk Mitigation: Regular assessments help identify and address vulnerabilities before malicious actors can exploit them, reducing the risk of data breaches and cyberattacks.
- Improved Security Posture: By identifying and addressing weaknesses, organizations can continuously improve their security posture, making it harder for attackers to gain unauthorized access.
- Compliance and Regulation: Regular audits and penetration tests assist organizations in meeting compliance requirements and industry standards related to data protection and security.
- Cost-Effectiveness: Early identification of vulnerabilities through testing and audits saves money by avoiding potential data breaches and the associated costs of incident response and recovery.
- Strengthened Customer Trust: Demonstrating a commitment to security through regular audits and testing instills trust among users and customers, enhancing the application's reputation.
- Enhanced Incident Response Preparedness: The findings from audits and penetration tests can help organizations develop effective incident response plans, allowing for a quicker and more efficient response to security incidents.
- Preventing Business Disruption: Proactively identifying and remediating vulnerabilities helps prevent potential disruptions to the business caused by cyberattacks or data breaches.
In conclusion, regular security audits and penetration testing are vital for maintaining a strong and secure web application. These practices allow organizations to stay ahead of cyber threats, protect sensitive data, and build a resilient defense against evolving cybersecurity challenges. By integrating these measures into their cybersecurity strategy, developers and organizations can ensure that their web applications remain trustworthy and secure for their users.
7️⃣ Monitoring & Incident Response

Monitoring and incident response are critical components of a robust cybersecurity strategy for web applications. While preventive measures are essential, no security system is infallible, and breaches or incidents may still occur. Effective monitoring and incident response help organizations detect and respond to security threats promptly, minimizing the impact of potential breaches and restoring normal operations swiftly. Let's explore the importance and best practices of monitoring and incident response:
A) Monitoring:
Monitoring involves actively observing the web application's behavior, network traffic, and user activities to detect any suspicious or abnormal patterns. The primary goals of monitoring are:
Early Threat Detection: Real-time monitoring enables organizations to identify security threats as soon as they occur or shortly after, allowing for immediate action.
Anomaly Detection: Monitoring tools can recognize unusual patterns, such as unusual login attempts or data access, which could indicate a potential security breach.
Performance Optimization: Monitoring also helps identify performance issues and bottlenecks, enhancing the overall user experience.
Compliance & Audit: Monitoring provides valuable data for compliance audits and regulatory requirements, ensuring that the application meets necessary security standards.
Best Practices for Monitoring:
✅ Implement continuous monitoring tools and solutions that cover both network and application layers.
✅ Set up alerts and notifications to promptly respond to any security events or anomalies.
✅ Monitor user activities, access logs, and authentication attempts to detect unauthorized access attempts.
✅ Monitor for unusual data access or data exfiltration to identify potential data breaches.
✅ Regularly review logs and monitor security metrics to detect and respond to threats effectively.
B) Incident Response:
Incident response refers to the coordinated approach taken by organizations to manage and mitigate the impact of a security incident or breach. The key objectives of incident response are
- Swift Response: A well-defined incident response plan enables organizations to respond quickly to security incidents, minimizing the damage caused.
- Containment & Mitigation: Incident response involves identifying the extent of the incident and taking steps to contain and mitigate the impact.
- Forensic Analysis: Incident response includes a forensic investigation to determine the cause, scope, and extent of the incident.
- Communication & Notification: Effective communication is vital during incident response, ensuring that stakeholders are informed about the situation and necessary actions are taken.
Best Practices for Incident Response:
✅Develop a comprehensive incident response plan that outlines roles, responsibilities, and communication procedures during a security incident.
✅Conduct regular incident response drills and simulations to ensure that the response team is prepared and can act efficiently in real-life scenarios.
✅Implement an escalation process to ensure that critical incidents are escalated to the appropriate personnel promptly.
✅Maintain an incident response playbook that includes step-by-step guidelines for responding to various types of security incidents.
✅After an incident is resolved, conduct a post-incident review to identify lessons learned and make improvements to the incident response plan.
By combining effective monitoring practices with a well-defined incident response strategy, organizations can better defend against security threats, respond to incidents promptly, and ultimately strengthen the security posture of their web applications.
8️⃣ Educating Users about Cybersecurity

Educating users about cybersecurity is crucial in today's digital age, where individuals are increasingly reliant on technology and online services. Many cyber threats target end-users through techniques like phishing, social engineering, and malware attacks. By raising awareness and providing cybersecurity education, we empower users to become more vigilant, responsible, and active participants in protecting their online safety and privacy. Here are some key points to consider when educating users about cybersecurity:
- Online Safety Best Practices: Teach users about fundamental online safety practices, such as creating strong and unique passwords, enabling two-factor authentication (2FA), and avoiding suspicious links or attachments in emails.
- Phishing Awareness: Educate users about phishing emails, which often attempt to trick them into revealing sensitive information or clicking on malicious links. Teach them to verify email senders, avoid sharing personal information via email, and be cautious of unexpected requests.
- Social Engineering Awareness: Raise awareness about social engineering tactics, where attackers manipulate users into divulging confidential information. Teach users to be skeptical of unsolicited phone calls, messages, or in-person requests for sensitive data.
- Safe Web Browsing: Guide users on safe web browsing practices, such as ensuring websites use HTTPS, avoiding suspicious or untrusted websites, and being cautious when downloading files from the internet.
- Mobile Device Security: Educate users on securing their mobile devices, including setting up screen locks, installing reputable apps from official stores, and regularly updating their devices' operating systems.
- Data Protection & Privacy: Emphasize the importance of protecting personal information and data privacy. Encourage users to be mindful of the information they share online and to review and manage app permissions and privacy settings.
- Secure Wi-Fi Usage: Advise users on the risks of using public Wi-Fi networks and the importance of using virtual private networks (VPNs) when accessing sensitive information over public networks.
- Security Updates & Patching: Educate users about the significance of updating their operating systems, applications, and antivirus software regularly. These updates often contain critical security patches to address vulnerabilities.
- Secure Email & Messaging: Inform users about secure email practices, including using encrypted email services and being cautious about sharing sensitive information via email or messaging platforms.
- Reporting Incidents: Encourage users to report suspicious activities, phishing attempts, or any potential security incidents to the appropriate IT or security personnel promptly.
- Ongoing Training & Awareness: Cybersecurity education should be an ongoing effort, with regular training sessions, reminders, and updates on emerging threats to keep users informed and vigilant.
- Real-Life Examples & Scenarios: Using real-life examples and scenarios helps users understand the relevance and impact of cybersecurity practices. Share stories of successful cyberattacks and their consequences to drive home the importance of cybersecurity.
By investing in cybersecurity education, organizations and individuals can create a safer digital environment. Empowered with knowledge and awareness, users become a crucial line of defense against cyber threats, contributing to a more secure online ecosystem for everyone.
Conclusion
The intersection of cybersecurity and web development is a critical aspect of building web applications that can withstand ever-evolving cyber threats. By following best practices for secure web applications, developers can create a safer online environment for users and protect their organizations from potential data breaches and cyberattacks. As technology advances and threats evolve, ongoing education and proactive security measures will continue to be paramount in the world of web development.
Remember to emphasize the practicality of these best practices with real-world examples and tips for implementation. Additionally, highlight the importance of collaboration between developers, security experts, and stakeholders to ensure that security remains a top priority throughout the web development process.
Thank you for reading, I hope this guide helps. Happy Coding👋🏾.


